Can a Trojan virus track you
Trojans are disguised as legitimate files, but they have one goal: to trick you into clicking, opening or installing them. If they're successful, this triggers the Trojan to download malware onto your device or begin spying on you.
Can Trojans be spyware
Trojan spyware looks and feels like a verifiable application and seeks to convince network users to click and load or execute the malware on their devices. Trojan malware used to be relatively easy to detect.
Can Trojan virus steal information
If you've found yourself in this situation, or even thinking you are, there's a real possibility you could have a Trojan virus on your computer. Trojan viruses can not only steal your most personal information, they also put you at risk for identity theft and other serious cybercrimes.
Is Trojan virus easy to detect
Running a malware scanner is the best way to detect and remove the trojan horse from the computer. Just look for a trusted and effective malware scanner software online. There are different malware scanners available for download, but choose the one that can protect your computer from advanced types of malware.
Can Trojan infect your WIFI
A trojan attack tricks you into downloading malware hiding a virus that then tramples all over your phone, tablet, or computer. A router virus can ride inside a trojan, waiting to sniff out vulnerable public or home Wi-Fi networks to infect.
Is Trojan spyware alert real
No, a Trojan spyware alert is a pop-up that aims to trick users into believing it's legitimate by pretending to be Windows or Apple.
Can Trojan hack my accounts
Malware is malicious software that can infect your computer and execute harmful actions without your permission. The term is quite broad and covers different threats like virus, trojan, spyware, and ransomware. Unfortunately, some types of malware may indeed allow a hacker to access and take over your email account.
Does VPN protect against Trojans
A VPN secures your Wi-Fi connection from man-in-the-middle attacks, but it can do very little to prevent malware infections. It can't protect you from viruses and other similar threats. What a VPN can do is encrypt the data you send and receive.
Can a Trojan steal my passwords
There are a variety of types of Trojans, many of which can launch sophisticated and clever attacks. Here are some types to be aware of: Password-stealing Trojans—These look for saved passwords on your computer and email them to the hackers. Some can even steal passwords cached in your browser history.
Is Trojan virus hard to remove
Can Trojan viruses be removed Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
Can Trojan viruses steal passwords
There are a variety of types of Trojans, many of which can launch sophisticated and clever attacks. Here are some types to be aware of: Password-stealing Trojans—These look for saved passwords on your computer and email them to the hackers. Some can even steal passwords cached in your browser history.
Are some Trojan viruses safe
Are Trojan viruses bad Trojan viruses are bad because they trick users into downloading malware that harms devices in various ways. As an example, remote access Trojans (RATs) give hackers remote access to infected computers, which can result in spying, data theft, and identity theft.
Can Trojan hack your account
Trojan viruses are bad because they trick users into downloading malware that harms devices in various ways. As an example, remote access Trojans (RATs) give hackers remote access to infected computers, which can result in spying, data theft, and identity theft.
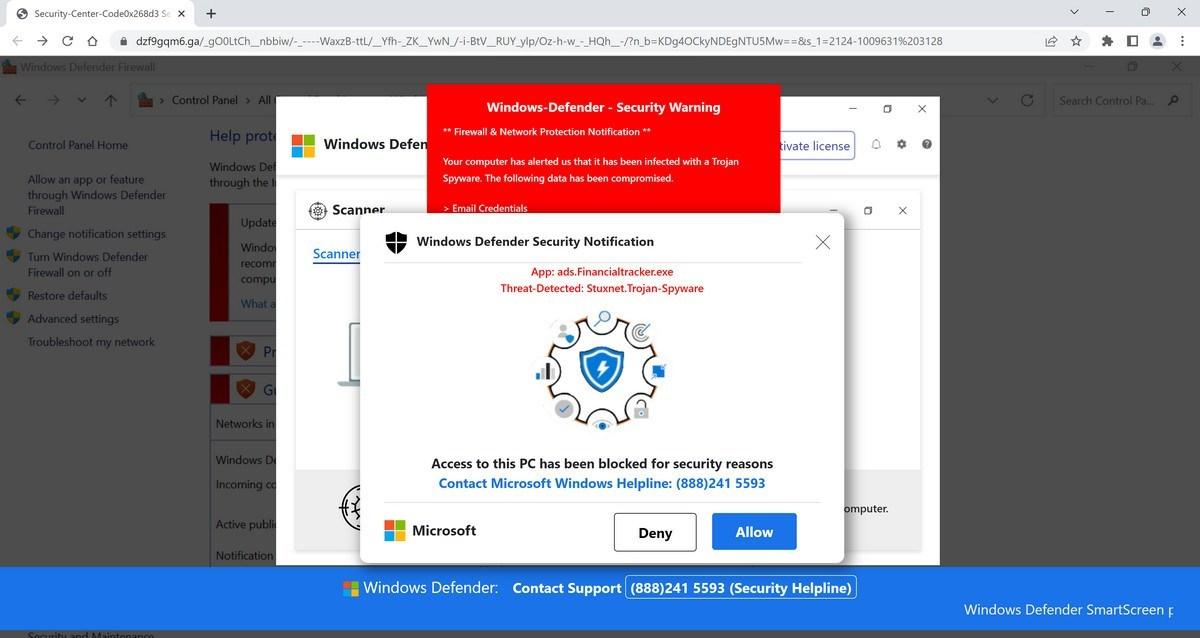
What is a Trojan fake alert
Trojan:JS/FakeAlert is the detection for a webpage that displays a fake scanning interface alerting the user that infected files have been found when none actually exist.
Do Trojans steal passwords
There are a variety of types of Trojans, many of which can launch sophisticated and clever attacks. Here are some types to be aware of: Password-stealing Trojans—These look for saved passwords on your computer and email them to the hackers. Some can even steal passwords cached in your browser history.
Can Trojans spread through Wi-Fi
A trojan attack tricks you into downloading malware hiding a virus that then tramples all over your phone, tablet, or computer. A router virus can ride inside a trojan, waiting to sniff out vulnerable public or home Wi-Fi networks to infect.
Do Trojans destroy data
A Trojan Horse (Trojan) is a type of malware that disguises itself as legitimate code or software. Once inside the network, attackers are able to carry out any action that a legitimate user could perform, such as exporting files, modifying data, deleting files or otherwise altering the contents of the device.
Can Trojan virus hack WIFI
Trojan Attacks
A trojan attack tricks you into downloading malware hiding a virus that then tramples all over your phone, tablet, or computer. A router virus can ride inside a trojan, waiting to sniff out vulnerable public or home Wi-Fi networks to infect.
Do Trojans delete data
Just some of the things that a Trojan may do include copying, modifying, blocking, or deleting data, or disrupting computer or network performance.
How bad is a Trojan
Trojan viruses are some of the most common malicious threats that impersonate legitimate software. That's why it can be difficult to notice them. Trojan viruses can steal your personal information, give external hackers control over your computer or mobile devices, add them to a botnet, or disrupt their performance.
Is Trojan virus real or fake
Trojans are deceptive programs that appear to perform one function, but in fact perform another, malicious function. They might be disguised as free software, videos or music, or seemingly legitimate advertisements.
Is Trojan a hacker
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users' system access with their software.
Is a Trojan virus bad on phone
Impact. Once the trojan is installed on the device, it silently performs its actual, unauthorized functions, which may range from harvesting personal data from the device, to sending premium SMS messages or intercepting SMS messages, connecting the device to a botnet and so on.
Does deleting a Trojan get rid of it
Can Trojan viruses be removed Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
Can Trojan destroy your computer
Trojan attacks have been responsible for causing major damage by infecting computers and stealing user data. Well-known examples of Trojans include: Rakhni Trojan: The Rakhni Trojan delivers ransomware or a cryptojacker tool—which enables an attacker to use a device to mine cryptocurrency—to infect devices.