What is cybersecurity phishing
Definitions: A technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a web site, in which the perpetrator masquerades as a legitimate business or reputable person.
What is the meaning of the word phished
: the practice of tricking Internet users (as through the use of deceptive email messages or websites) into revealing personal or confidential information which can then be used illicitly. The most common form …
Is phishing a cyber crime
As of 2020, it is the most common type of cybercrime, with the FBI's Internet Crime Complaint Center reporting more incidents of phishing than any other type of computer crime.
What is the difference between spoofing and phishing
Spoofing is a technique used to disguise the sender's identity, while phishing is a method used to trick the recipient into divulging personal information or performing an action.
Is phishing a crime
Phishing is a cyber crime that leverages deceptive emails, websites, and text messages to steal confidential personal and corporate information. Victims are tricked into giving up personal information such as their credit card data, phone number, mailing address, company information, etc.
Is phishing a virus
Phishing is a type of cybercrime where attackers pose as a trusted or legitimate business to dupe an individual into sharing information such as bank account numbers, credit card details, login credentials and other sensitive data, and/or to download a phishing virus onto the user's computer.
Is phishing illegal UK
While the phishing email is not a computer misuse offence – it is a form of fraud – accessing the accounts with the collected passwords and usernames is a computer misuse offence, and is often used to facilitate further crimes.
Is phishing a virus or not
Phishing is a type of cybercrime where attackers pose as a trusted or legitimate business to dupe an individual into sharing information such as bank account numbers, credit card details, login credentials and other sensitive data, and/or to download a phishing virus onto the user's computer.
Why is spoofing illegal
When is spoofing illegal Under the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value. Anyone who is illegally spoofing can face penalties of up to $10,000 for each violation.
What are 3 common types of spoofing
The 4 Main Types of Spoofing Attacks and How to Prevent ThemEmail Spoofing. Let's say you receive an email claiming to be from your bank, and it says that you need to log in to your online banking account and change your password.Website Spoofing.IP Spoofing.DNS spoofing.
Is it illegal to spoof emails
In some cases, spoofers may imitate their contact information, IP addresses, or other identifiers to protect their corporate identity. However, if the spoofer carries out fraud to defraud a person or institution, this is illegal and can result in fines and even prison terms.
Is phishing a Trojan
Phishing-trojans are document files that are specially-crafted to look legitimate, but serve as delivery vehicles for harmful programs.
Is IP phishing legal
IP spoofing FAQs
As long as you live in a country where VPNs are legal, then you aren't breaking any laws by using one. Once the spoofing is used for criminal activity, then it becomes illegal.
Why do people hack
While some hackers do it for fame, because they're disgruntled ex-employees or because they view hacking as sport, the majority of cyber criminals do it for the money. Verizon's 2022 Data Breach Investigations Report found that 86% of the data breaches they analysed were financially motivated.
Who invented phishing
spammer Khan C. Smith
Famous hacker and spammer Khan C. Smith is credited to have coined the term phishing. He first introduced the term “phishing” in the Usenet newsgroup after AOL rolled out measures to prevent using fake, algorithmically generated credit card numbers to open accounts.
Is spoofing bad for your PC
Spoofed emails often request a money transfer or permission to access a system. Additionally, they can sometimes contain attachments that install malware — such as Trojans or viruses — when opened. In many cases, the malware is designed to go beyond infecting your computer and spread to your entire network.
Why can’t we stop spoofing
Since spoofing services typically generate numbers randomly, there's no surefire way to prevent a phone number spoofer from using your caller ID.
What is spoofing techniques
Spoofing is a technique through which a cybercriminal disguises themselves as a known or trusted source. Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
Is email spoofing easy
Email spoofing is a threat that involves sending email messages with a fake sender address. Email protocols cannot, on their own, authenticate the source of an email. Therefore, it is relatively easy for a spammer or other malicious actors to change the metadata of an email.
Can hackers spoof email
Email spoofing is possible due to how email systems are designed. The client application assigns a sender address to outgoing messages, so outgoing email servers cannot identify whether the sender address is legitimate or spoofed. Recipient servers and antimalware software can help detect and filter spoofed messages.
Is Trojan virus real or fake
Trojans are deceptive programs that appear to perform one function, but in fact perform another, malicious function. They might be disguised as free software, videos or music, or seemingly legitimate advertisements.
Is Trojan virus real
One form of Trojan malware has targeted Android devices specifically. Called Switcher Trojan, it infects users' devices to attack the routers on their wireless networks. The result Cybercriminals could redirect traffic on the Wi-Fi-connected devices and use it to commit various crimes.
Is VPN a spoofing
Spoofing your location is just another term for faking or hiding your location. This requires changing your IP address. One of the easiest ways to spoof your location is to use a VPN. This allows you to connect to a server in another country and obtain a different IP address.
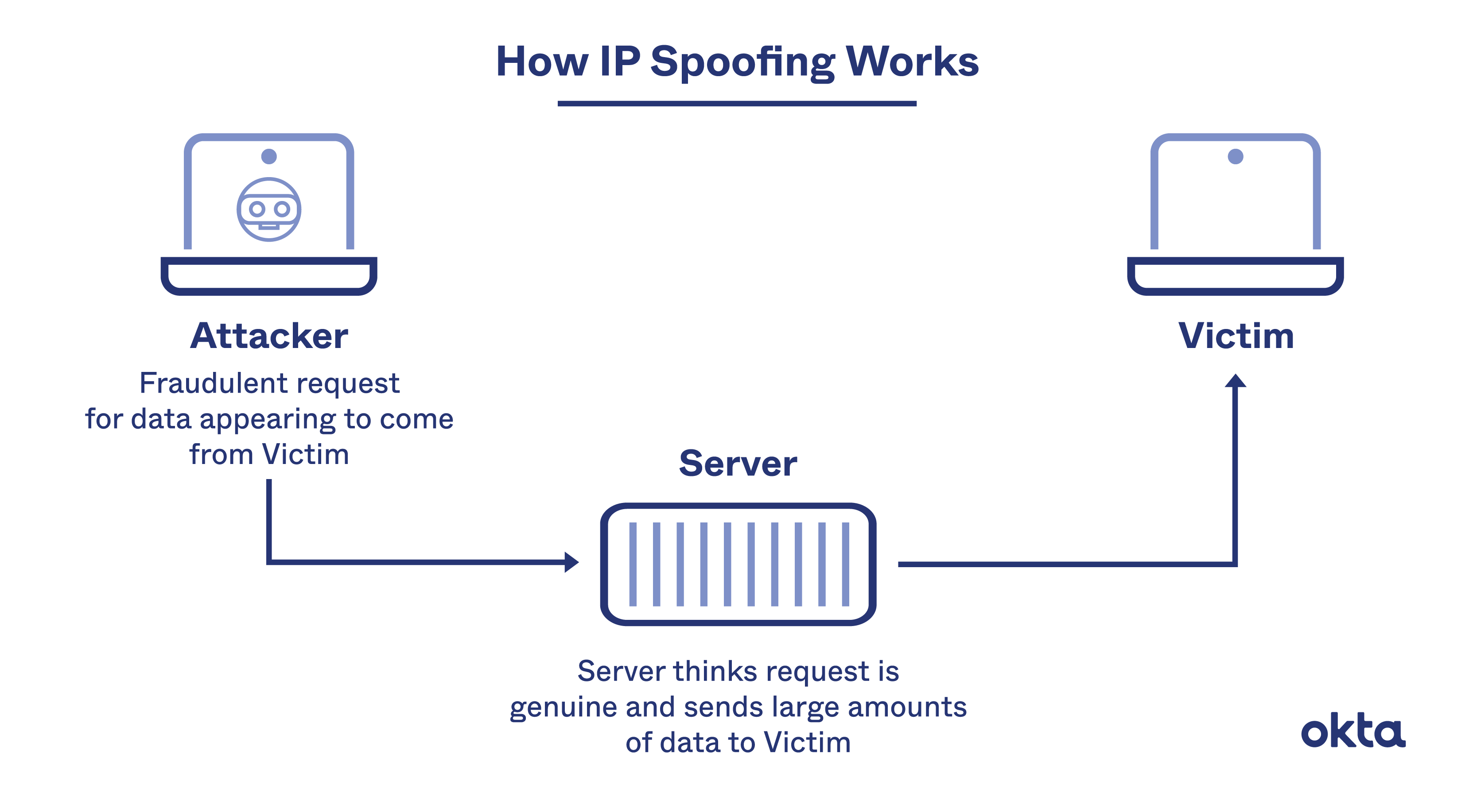
How easy is IP spoofing
To accomplish IP spoofing, a hacker typically needs: A trusted connection. Spoofs work best between two devices that have some kind of prior relationship. If a hacker can access an internal machine that doesn't require a login, the attack is much easier to launch.
Do hackers learn to hack
Most hackers have to do a lot of research before they can attempt to actually hack professionally. Trial and error. A key element in learning how to hack is by using trial and error. Many hackers use programs to test their hacking capabilities.