Is spoofing a cyber crime
IP address spoofing hides the true identity and location of the computer or mobile device used by the cyber criminal. Cyber criminals might spoof an IP address for a network that uses IP address authentication, making it easy to access the network.
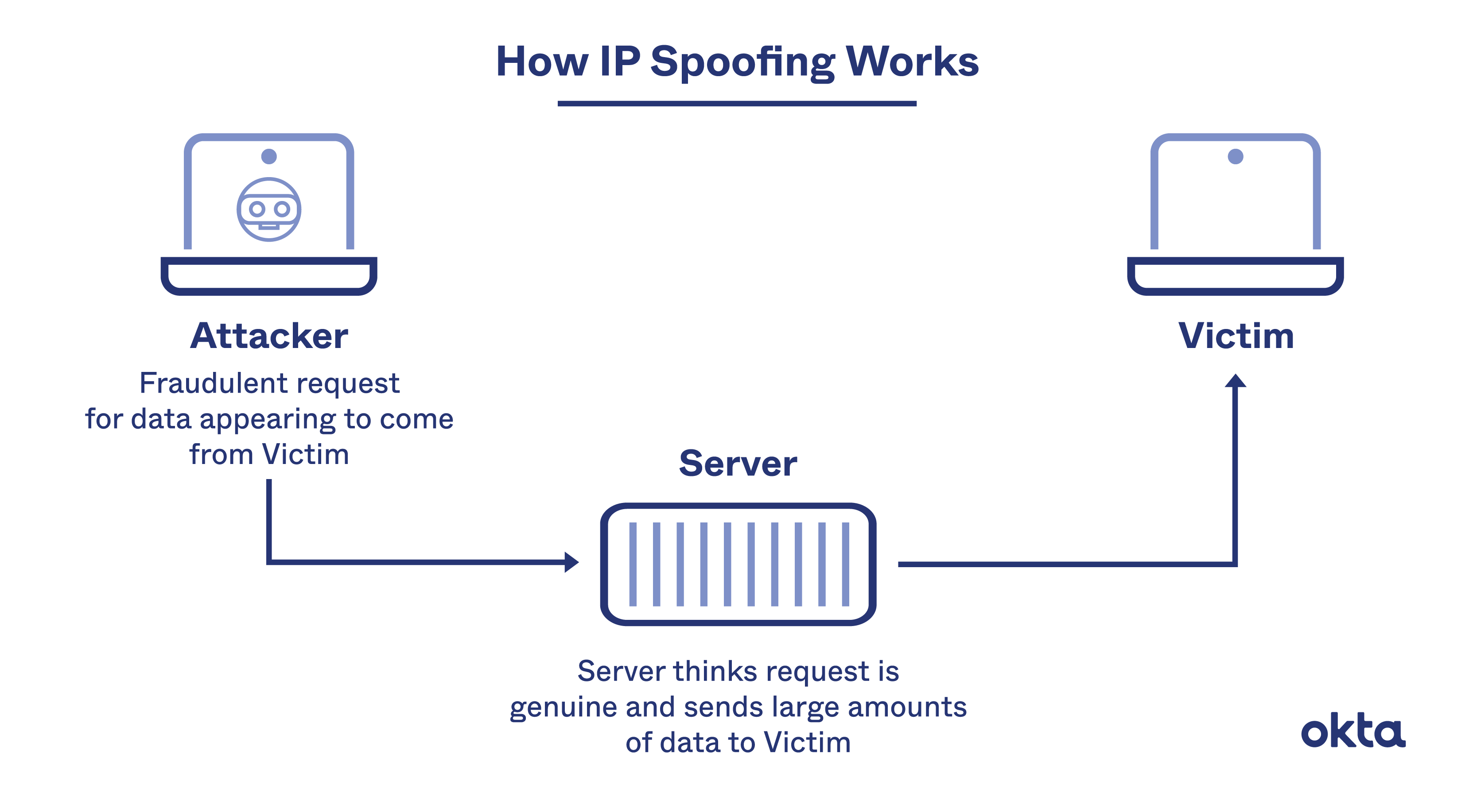
What is IP spoofing in cyber crime
IP spoofing, or IP address spoofing, refers to the creation of Internet Protocol (IP) packets with a false source IP address to impersonate another computer system. IP spoofing allows cybercriminals to carry out malicious actions, often without detection.
Is it illegal to spoof IP address
IP spoofing, as a whole, isn't illegal. You may have legitimate reasons for deploying the technique within your own server. For example, if you're preparing to launch a new website, you must understand how it will perform when hit by hundreds or even thousands of website visitors from all around the globe.
What type of attack is spoofing
Spoofing is the act of disguising a communication or identity so that it appears to be associated with a trusted, authorized source. Spoofing attacks can take many forms, from the common email spoofing attacks that are deployed in phishing campaigns to caller ID spoofing attacks that are often used to commit fraud.
Why is spoofing not illegal
If the number correctly represents the party who is making the call, if it is showing the name of the business as part of the caller ID, and if you can call it back, then it is legal, even if the number is spoofed.
What type of crime is cyber
Cybercrime is criminal activity that either targets or uses a computer, a computer network or a networked device. Most cybercrime is committed by cybercriminals or hackers who want to make money.
Is IP spoofing the same as IP hijacking
Spoofing and hijacking are similar, but there are some differences worth pointing out. A spoofing attack (see Chapter 4, “Spoofing”) is different from a hijack in that an attacker is not actively taking another user offline to perform the attack. Instead, he pretends to be another user or machine to gain access.
What is an example for spoofing in cyber crime
Fake job offers, fake banking-related messages, fake lottery messages, money refund scams, and password reset messages are some examples of Text Message Spoofing. Spoofed messages are difficult to identify until the person is aware of where to look for them. The sender's name cannot be clicked and replied.
Is VPN a spoofing
A VPN is the most common type of IP spoofing. Although it's not technically an attack, it employs the same principles. A VPN will hide your real IP address so you can move around the internet without anyone knowing where you're located.
How do hackers spoof IP
In IP spoofing, a hacker uses tools to modify the source address in the packet header to make the receiving computer system think the packet is from a trusted source, such as another computer on a legitimate network, and accept it. This occurs at the network level, so there are no external signs of tampering.
Is IP spoofing a passive attack
Packet Spoofing is the dynamic presentation of fake network traffic that impersonates someone else. Packet Sniffing is a passive attack since attackers cannot mutilate the system in any way. In packet Spoofing, stackers inject malicious software into the victim's system.
Is spoofing a security threat
Spoofing is a sort of fraud in which someone or something forges the sender's identity and poses as a reputable source, business, colleague, or other trusted contact in order to obtain personal information, acquire money, spread malware, or steal data.
Why is IP spoofing bad
IP Spoofing is a hacker's fake ID. It lets them use a fake IP address to conceal their identity and the true source of their device. With IP spoofing, hackers can infect your device with malware, steal sensitive information, or flood websites with DDoS attacks.
Why is IP spoofing possible
Internet Protocol (IP) spoofing is a type of malicious attack where the threat actor hides the true source of IP packets to make it difficult to know where they came from. The attacker creates packets, changing the source IP address to impersonate a different computer system, disguise the sender's identity or both.
Which is not a cyber crime
Online gaming is not a cybercrime.
A crime that does not involve a computer, a network and a networked device is not a cybercrime. In cybercrime, a computer may have been used to target the victim. Some examples of cybercrime are Phishing, Cyberstalking, Spoofing, Privacy breach, Data breach, identity theft, etc.
Which is not a type of cyber crime
Explanation: Installing antivirus in a computer system is not considered a crime because antivirus secures the device from spyware, malware, and viruses. These viruses and malware lead to online fraud, phishing, harassment, theft, etc.
Is VPN considered IP spoofing
A VPN is the most common type of IP spoofing. Although it's not technically an attack, it employs the same principles. A VPN will hide your real IP address so you can move around the internet without anyone knowing where you're located.
What is the difference between IP spoofing and phishing
Differences Between Spoofing and Phishing
Purpose: The goal of spoofing is to impersonate someone's identity while the purpose of phishing attacks is to steal information.
What is IP spoofing in real life example
For example, companies may use IP spoofing to test websites when they go live, simulating external traffic to the site. Security personnel also use spoofing see how their systems respond to different types of attacks. Learn about other common types of cyber attacks and ways to prevent them.
What is spoofing and why is it illegal
It is often used as a means to gain access to confidential information, which can be used to facilitate criminal activities. For example, a spoofed email from a bank could prompt a user to enter their login credentials into a fake website, allowing the attacker to steal sensitive data.
Can police track a fake VPN
There is no way to track live, encrypted VPN traffic.
That's why police or government agencies who need information about websites you visited have to contact your internet service provider (ISP for short), and only then your VPN provider.
Is spoofing a virus
Spoofing occurs when a scammer poses as a trusted source to obtain access to your identity or assets. Spoofers perform various spoofing attacks so they can steal personal information, money, or infect your device with malware.
How easy is IP spoofing
End users have a difficult time detecting IP spoofing. These attacks are carried out at the network layer — Layer 3 of the Open Systems Interconnection communications model. That way, there aren't external signs of tampering. The spoofed connection requests look like legitimate connection requests externally.
Does VPN protect against spoofing
Man-in-the-middle attacks
A VPN hides your internet activity, keeping you safe from attack. MITM attacks include evil twins, WiFi sniffing, and DNS spoofing.
Is spoofing an active attack
Domain spoofing is when an attacker creates a website that mimics an existing site – often by slightly changing domain names. The goal of these attacks is to have users attempt to log into their account, at which point the attacker can record their account credentials or other personal information.